|
OBJECTIVE |
For HRDs to appreciate layering their security |
|
TIMING |
75 minutes |
|
TIME BREAKDOWN |
Introduction - 15 minutes |
| MATERIALS NEEDED |
Flip charts & marker pens |
When planning and facilitating this session, it is important to consistently apply an intersectional lens to each participant's identity and experiences, and their protection needs. Overlapping systems of discrimination and privilege, such as gender, sexual orientation, religion, disability, racial and/or ethnic origin, economic status/class, marital status, citizenship, age and physical appearance, can have a profound impact on human rights defenders' and their communities' perception of and experience with risks and protection.
Introduction:
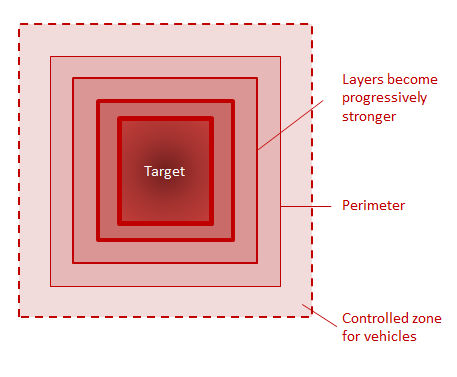
Improving security can be achieved by multi-layering and using different measures – known as layered security, or defence-in-depth.
You can offer examples of a rope, the more threads in the rope there are, the stronger the rope is.
You can also bring the participants to think of an obstacle course that the adversary needs to run – the more obstacles and layers there are, the harder it is to achieve their objectives.
Or an onion with many layers that the adversary needs to peel back – with the HRD in the middle of it.

The principle of layered security could apply to:
- the number of relevant mitigation measures identified during risk assessment (the more relevant mitigation measures for reducing likelihood and impact you have for a particular threat, the stronger your plan will be),
- digital security (a series of defence measures to protect data including password management, encryption, offshore hosting, access management to data, firewalls, antivirus, auditing, etc)
- site planning (refer below for layering a site plan). This means looking at your office or home from a bird’s eye view, and make more and more layers.
Layered security is a recognition that there is strength in the measures working together. There is no security measure by itself that cannot be defeated as they all have vulnerabilities eg. If a HRD installs CCTV, an adversary can cut the power, use masks, find blind spots etc. It is in their combination within your security strategy that you find strength. There is also strength in the HRD expecting each measure to be overcome, and then having a backup. If they cut the power, I will have a torch and battery lights. If they cut power to the CCTV, I will have battery backup through an Uninterruptible Power Supply battery. If they jump over the fence, they will face my dog. If they get through my dog, I have a strong door and lock system with solar movement detection lighting. If they break through my door, I have alarms and access control systems. If they break through this system, I have practised what to do (safe room or evacuation plan).
A site could be a house or apartment, your office, a cafe you like, or your family home. For site planning of layered security:
Think of the site as 4 zones. Then layer in all these zones.
- First zone of defence: Outside the site boundary (outside the main walls/fences)
- Second zone of defence: Between the perimeter and the house/office (for instance a front garden, between gate and the front door
- Third zone of defence: Inside the building (the office/home)
- Fourth zone of defence: Safe room inside building/evacuation plans
Exercise for Participants:
STEP 1: Draw, from a bird’s eye perspective, your home or office, or community/village.
STEP 2: Divide the site into 4 the zones (outside perimeter, between perimeter and building, inside building, inside safe room / evacuation plan).
STEP 3: Identify the various layers of security, in each zone, that you currently have.
STEP 4: Imagine yourself as the adversary, approaching the selected site (office or home or community). How will can your measures be defeated? What would you do, as the adversary? This should also highlight the importance of HRDs doing simulation exercises when they return to their offices/homes/communities
STEP 5: Take a different coloured pen, and write down extra layers that you could include in your security plan for your home/office/community. Or identify improvements to existing layers to reduce the vulnerabilities.
Conclusion:
If an adversary is determined or professional (eg state actor), they will not see a perimeter fence and just leave. They will look for vulnerabilities such as to climb the fence, or climb a tree over the fence. Then what will they face? A guard? What if the adversary waits until the guard goes to the bathroom or stops concentrating? Essentially, ask the HRDs to take a pessimistic mindset to each of their measures, and predict that they will be defeated by their determined adversary. For example, what obstacles are there in front of them? The more obstacles, the stronger their security plan.
The conclusion can include the fact that protection of premises is a key element, and other sessions will consider places where other threats could be realised, eg travelling.
Notes for Trainers
STEP 2:
Sometimes HRDs won’t have all the zones. eg. I don’t have a wall to my house, our community doesn’t have a perimeter. The principle is ask them to identify the point in which the adversary has entered their space. HRDs need to define what ‘their space’ is. It could be the moment someone crosses a bridge into the community territory, or the moment they drive along a long driveway.
Examples could include any of the following security mitigation measures:
Zone 1:
- We’ve done actor mapping of our neighbours and community members - we know who will help us
- We chose a safe neighbourhood for the office
- We have good lighting on the street outside the home
- We use mirrors to see around corners
- Concrete walls which are 3m tall
- Hostile fence toppings (razor wire, electrical wiring, glass etc)
- Front gate always closed
- Strong access control
- CCTV outside the front gate
- The community is very security aware (behavioural, not equipment)
- If a community or village, we have a checkpoint to stop people to ask who they are, with radios to call ahead
- We use an intercom for visitors
- Front gate always locked
- We cut down the tree branches overhanging the walls so no-one can climb in
- We have a rule that we always walk out to our car in pairs
- Automatic gates
Zone 2:
- We have a dog
- We have movement sensor lighting
- Perimeter Intrusion Detection Systems
- There is a Passive Infrared or Active Infrared alarm in the front yard
- We have CCTV for the garden. We have activated movement detection in the cameras
- The front door is alarmed
Zone 3:
- Inside the office we have alarms
- There are strong doors that delay an adversary
- Security door
- Finger print access control
- Bars on the windows
- We always keep the front door locked
- Our community has meetings every week about security planning
- Our community has informal security guards
- We use drums or bang pots to notify of an attacker
- HRDs are given training on opening doors
Zone 4:
- Safe room or strong room prepared
- We have an identified evacuation plan
- We practice what would happen if the police were to come to arrest us or do a raid
- We have the numbers of people to call when there’s a problem (friends who will come, lawyers, international NGOs)
STEP 3:
When looking at HRDs’ existing capabilities, you can prompt them to think of five different types of security measures:
- the environment / location in which it is located
- eg we chose a safe neighbourhood, the street lighting is good, our neighbours are our friends and will let us know if there's a problem etc
- structural issues - physical aspects of the entire building and the office buildings
- walls (height, transparent, materials etc), barriers, rivers in the community, big property or large open spaces
- practices / procedures / policies in terms of behaviour
- (our guards check ID, our staff don’t open the door unless the visitor can be seen, we have a documented security policy etc)
- equipment to enhance and systematize security
- doors, windows bars, locks, alarms, automatic closing doors, remote controlled gates, radios, CCTV etc
- training and experience
- we give staff training in evacuation, my family know first aid, I know self defence, we have had police raids in the past so know what to do etc)
STEP 4:
The HRD should be asked to think like their adversary. As Sun Tzu said ‘Know thy enemy’
How will the adversary overcome overcome each of the security measures? Once the HRD has identified their vulnerabilities, they can then start to fix them, and then have back ups and more and more layers.
STEP 5:
They can share these with the group, ask for suggestions, share strategies etc.
